mirror of
https://github.com/pomerium/pomerium.git
synced 2025-07-07 11:58:12 +02:00
Deferential to Google's own docs since they keep changing the screens. Signed-off-by: Bobby DeSimone <bobbydesimone@gmail.com> |
||
|---|---|---|
| .. | ||
| community | ||
| identity-providers | ||
| img | ||
| quick-start | ||
| topics | ||
| architecture.md | ||
| background.md | ||
| CHANGELOG.md | ||
| FAQ.md | ||
| installation.md | ||
| readme.md | ||
| upgrading.md | ||
| title | lang | sidebarDepth | meta | |||||
|---|---|---|---|---|---|---|---|---|
| What is Pomerium? | en-US | 0 |
|
What is Pomerium
Overview?
Pomerium is an identity-aware proxy that enables secure access to internal applications. Pomerium provides a standardized interface to add access control to applications regardless of whether the application itself has authorization or authentication baked-in. Pomerium gateways both internal and external requests, and can be used in situations where you'd typically reach for a VPN.
Pomerium can be used to:
- provide a single-sign-on gateway to internal applications.
- enforce dynamic access policy based on context, identity, and device state.
- aggregate access logs and telemetry data.
- perform delegated user authorization for service-based authorization systems:
- provide unified identity attestation for upstream services:
- provide a VPN alternative.
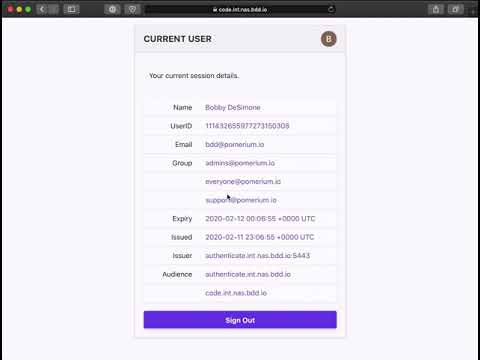
Demo
To make this a bit more concrete, click the image thumbnail to see a short youtube demo:
The above video shows the flow for both an unauthorized and authorized user.
- An unauthorized user authenticates with their corporate single-sign-on provider.
- The unauthorized user is blocked from a protected resource.
- The unauthorized user signs out from their session.
- An authorized user authenticates with their corporate single-sign-on provider.
- Pomerium delegates and grants access to the requested resource.
- The authorized user inspects their user details including group membership.