mirror of
https://github.com/pomerium/pomerium.git
synced 2025-08-03 00:40:25 +02:00
init Enterprise documentation section
This commit is contained in:
parent
ac2cb31582
commit
e9209fed72
5 changed files with 126 additions and 3 deletions
|
|
@ -39,9 +39,9 @@ module.exports = {
|
|||
{ text: "Guides", link: "/guides/" },
|
||||
{
|
||||
text: "Enterprise",
|
||||
link: "https://www.pomerium.com/",
|
||||
target: "_self",
|
||||
rel: "",
|
||||
link: "/enterprise/",
|
||||
//target: "_self",
|
||||
//rel: "",
|
||||
},
|
||||
{
|
||||
text: "v0.14.x", // current tagged version
|
||||
|
|
@ -188,6 +188,20 @@ module.exports = {
|
|||
children: [""],
|
||||
},
|
||||
],
|
||||
"/enterprise/": [
|
||||
{
|
||||
title: "Enterprise",
|
||||
type: "group",
|
||||
collapsable: false,
|
||||
sidebarDepth: 0,
|
||||
children: [
|
||||
//"",
|
||||
"about",
|
||||
"install",
|
||||
"concepts",
|
||||
],
|
||||
},
|
||||
],
|
||||
},
|
||||
},
|
||||
}
|
||||
|
|
|
|||
17
docs/enterprise/about.md
Normal file
17
docs/enterprise/about.md
Normal file
|
|
@ -0,0 +1,17 @@
|
|||
---
|
||||
title: About
|
||||
sidebarDepth: 1
|
||||
description: What does the Pomerium Enterpise Console offer?
|
||||
---
|
||||
|
||||
# Pomerium Enterprise
|
||||
|
||||
This paragraph introduces what Pomerium Enterprise is.
|
||||
|
||||
## Features
|
||||
|
||||
## Availability
|
||||
|
||||
## Sign up
|
||||
|
||||
CTA
|
||||
15
docs/enterprise/concepts.md
Normal file
15
docs/enterprise/concepts.md
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
---
|
||||
title: Concepts
|
||||
sidebarDepth: 1
|
||||
description: Learn how the Pomerium Enterprise Console works.
|
||||
---
|
||||
|
||||
# Concepts
|
||||
|
||||
## Namespaces
|
||||
|
||||
## Routes
|
||||
|
||||
## Policies
|
||||
|
||||
### Authorization Policy
|
||||
32
docs/enterprise/install.md
Normal file
32
docs/enterprise/install.md
Normal file
|
|
@ -0,0 +1,32 @@
|
|||
---
|
||||
title: Installation
|
||||
sidebarDepth: 1
|
||||
description: How to install Pomerium Enterprise
|
||||
---
|
||||
|
||||
# Install Pomerium Enterprise
|
||||
|
||||
## Before You Begin
|
||||
|
||||
## Binaries
|
||||
|
||||
:::: tabs
|
||||
|
||||
::: tab deb
|
||||
__markdown content__
|
||||
:::
|
||||
|
||||
|
||||
::: tab rpm
|
||||
|
||||
:::
|
||||
|
||||
::: tab source
|
||||
|
||||
:::
|
||||
|
||||
::::
|
||||
|
||||
### System Service
|
||||
|
||||
## Initial Configuration
|
||||
45
docs/enterprise/readme.md
Normal file
45
docs/enterprise/readme.md
Normal file
|
|
@ -0,0 +1,45 @@
|
|||
---
|
||||
title: Pomerium Enterprise
|
||||
lang: en-US
|
||||
sidebarDepth: 0
|
||||
meta:
|
||||
- name: keywords
|
||||
content: >-
|
||||
pomerium overview identity-access-proxy beyondcorp zero-trust
|
||||
reverse-proxy ztn zero-trust-networks console enterprise scale
|
||||
---
|
||||
|
||||
# What is Pomerium
|
||||
|
||||
## Overview?
|
||||
|
||||
Pomerium is an identity-aware proxy that enables secure access to internal applications. Pomerium provides a standardized interface to add access control to applications regardless of whether the application itself has authorization or authentication baked-in. Pomerium gateways both internal and external requests, and can be used in situations where you'd typically reach for a VPN.
|
||||
|
||||
Pomerium can be used to:
|
||||
|
||||
- provide a **single-sign-on gateway** to internal applications.
|
||||
- enforce **dynamic access policy** based on **context**, **identity**, and **device state**.
|
||||
- aggregate access logs and telemetry data.
|
||||
- perform delegated user authorization for service-based authorization systems:
|
||||
- [Istio](/guides/istio.md)
|
||||
- [Google Cloud](/guides/cloud-run.md)
|
||||
- provide unified identity attestation for upstream services:
|
||||
- [Kubernetes](/guides/kubernetes.md)
|
||||
- [Grafana](/guides/istio.md#pomerium-configuration)
|
||||
- [Custom applications](/docs/topics/getting-users-identity.md)
|
||||
- provide a **VPN alternative**.
|
||||
|
||||
## Demo
|
||||
|
||||
To make this a bit more concrete, click the image thumbnail to see a short youtube demo:
|
||||
|
||||
[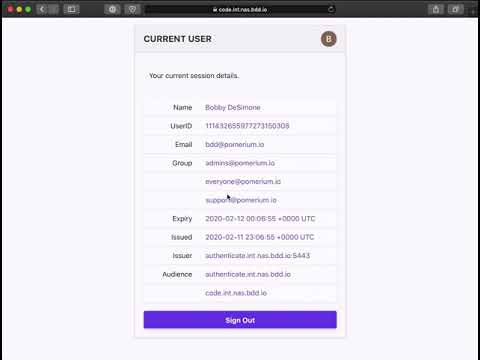](https://www.youtube.com/watch?v=ddmrkvBSO60 "Pomerium demo")
|
||||
|
||||
The above video shows the flow for both an unauthorized and authorized user.
|
||||
|
||||
1. An **unauthorized** user authenticates with their corporate single-sign-on provider.
|
||||
2. The **unauthorized** user is blocked from a protected resource.
|
||||
3. The **unauthorized** user signs out from their session.
|
||||
4. An **authorized** user authenticates with their corporate single-sign-on provider.
|
||||
5. Pomerium delegates and grants access to the requested resource.
|
||||
6. The **authorized** user inspects their user details including group membership.
|
||||
Loading…
Add table
Add a link
Reference in a new issue