mirror of
https://github.com/pomerium/pomerium.git
synced 2025-08-03 00:40:25 +02:00
Fixed links throughout
This commit is contained in:
parent
f0480feccb
commit
669b3e2a3d
23 changed files with 83 additions and 80 deletions
|
|
@ -41,8 +41,8 @@ Finally, source the configuration `env` file and run pomerium specifying the `co
|
|||
|
||||
Browse to `external-verify.your.domain.example`. Connections between you and [verify] will now be proxied and managed by Pomerium.
|
||||
|
||||
[configuration variables]: ../../reference/readme.md
|
||||
[configuration variables]: /reference/readme.md
|
||||
[download]: https://github.com/pomerium/pomerium/releases
|
||||
[verify]: https://verify.pomerium.com/
|
||||
[identity provider]: ../identity-providers/
|
||||
[tls certificates]: ../topics/certificates.md
|
||||
[identity provider]: /docs/identity-providers/readme.md
|
||||
[tls certificates]: /docs/topics/certificates.md
|
||||
|
|
|
|||
|
|
@ -71,8 +71,8 @@ make && ./bin/pomerium -config config.yaml
|
|||
|
||||
Browse to `verify.localhost.pomerium.io`. Connections between you and [verify] will now be proxied and managed by Pomerium.
|
||||
|
||||
[configuration variables]: ../../reference/readme.md
|
||||
[configuration variables]: /reference/readme.md
|
||||
[verify]: https://verify.pomerium.com/
|
||||
[identity provider]: ../identity-providers/
|
||||
[identity provider]: /docs/identity-providers/readme.md
|
||||
[make]: https://en.wikipedia.org/wiki/Make_(software)
|
||||
[tls certificates]: ../topics/certificates.md
|
||||
[tls certificates]: /docs/topics/certificates.md
|
||||
|
|
|
|||
|
|
@ -207,7 +207,7 @@ You can also navigate to the special pomerium endpoint `hello.localhost.pomerium
|
|||
|
||||
## Next Steps
|
||||
|
||||
Congratulations on installing Pomerium to your Kubernetes cluster! If you're installing Pomerium Enterprise next, see [Install Pomerium Enterprise Console in Helm]. If not, check our our [guides](/guides/) to install common services behind Pomerium.
|
||||
Congratulations on installing Pomerium to your Kubernetes cluster! If you're installing Pomerium Enterprise next, see [Install Pomerium Enterprise Console in Helm]. If not, check our our [guides](/guides/readme.md) to install common services behind Pomerium.
|
||||
|
||||
[cert-manager]: https://cert-manager.io/docs/
|
||||
[cert-manager: CA]: https://cert-manager.io/docs/configuration/ca/
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ description: This article describes various ways to install pomerium
|
|||
|
||||
Pomerium is shipped in multiple formats and architectures to suit a variety of deployment patterns. There are two binaries:
|
||||
|
||||
- `pomerium` is the primary server component. It is a monolithic binary that can perform the function of any [services mode](/reference/#service-mode).
|
||||
- `pomerium` is the primary server component. It is a monolithic binary that can perform the function of any [services mode](/reference/readme.md#service-mode).
|
||||
- `pomerium-cli` (optional) is a command-line client for working with Pomerium. Functions include acting as an authentication helper for tools like [kubtctl](topics/kubernetes-integration.md).
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -33,7 +33,7 @@ To prevent early session loss in production deployments, persistent storage back
|
|||
|
||||
## Backends
|
||||
|
||||
Configuration options for each backend are detailed in [databroker configuration reference](/reference/#databroker-service).
|
||||
Configuration options for each backend are detailed in [databroker configuration reference](/reference/readme.md#data-broker-service).
|
||||
|
||||
In all backends, Pomerium encrypts record values. This ensures security of all records at rest, regardless of data store capabilities. While this prevents many classes of attack vector, additional security measures should always be taken to secure data in transit and minimize access to the backends themselves.
|
||||
|
||||
|
|
|
|||
|
|
@ -43,14 +43,14 @@ Pomerium can be leveraged as a proxy for user requests to the API Server.
|
|||
Building on top of a standard Kubernetes and Pomerium deployment:
|
||||
|
||||
1. Pomerium is given access to a Kubernetes service account with [impersonation](https://kubernetes.io/docs/reference/access-authn-authz/authentication/#user-impersonation) permissions
|
||||
2. A [policy route](/reference/#policy) is created for the API server and [configured](/reference/#kubernetes-service-account-token) to use the service account token
|
||||
2. A [policy route](/reference/readme.md#policy) is created for the API server and [configured](/reference/readme.md#kubernetes-service-account-token) to use the service account token
|
||||
3. Kubernetes RoleBindings operate against IdP Users and Group subjects
|
||||
4. Users access the protected cluster through their standard tools, using [pomerium-cli](/docs/installation.md#pomerium-cli) as an auth provider in `~/.kube/config`
|
||||
4. Users access the protected cluster through their standard tools, using [pomerium-cli](/docs/releases.md#pomerium-cli) as an auth provider in `~/.kube/config`
|
||||
5. Pomerium authorizes requests and passes the user identity to the API server for fine grained RBAC
|
||||
|
||||
## Kubeconfig Setup
|
||||
|
||||
After installing the [pomerium-cli](/docs/installation.md#pomerium-cli), you must configure your `kubeconfig` for authentication.
|
||||
After installing the [pomerium-cli](/docs/releases.md#pomerium-cli), you must configure your `kubeconfig` for authentication.
|
||||
|
||||
Substitute `mycluster.pomerium.io` with your own API Server's `from` in Pomerium's policy:
|
||||
|
||||
|
|
|
|||
|
|
@ -6,13 +6,13 @@ description: >-
|
|||
|
||||
# Production Deployment
|
||||
|
||||
This page covers the topic of running Pomerium in a production configuration. See the [quick start section](../install/quickstart/) for canned example configurations.
|
||||
This page covers the topic of running Pomerium in a production configuration. See the [quick start section](/docs/install/readme.md) for canned example configurations.
|
||||
|
||||
Please also see [architecture](../#architecture) for information on component interactions.
|
||||
Please also see [architecture](/docs/architecture.md) for information on component interactions.
|
||||
|
||||
## Service Mode
|
||||
|
||||
For configuration of the service mode, see [Service Mode](../../reference/readme.md#service-mode).
|
||||
For configuration of the service mode, see [Service Mode](/reference/readme.md#service-mode).
|
||||
|
||||
### All in One
|
||||
|
||||
|
|
|
|||
|
|
@ -13,7 +13,7 @@ meta:
|
|||
|
||||
Operations and engineering teams frequently require access to lower level administrative and data protocols such as SSH, RDP, Postgres, MySQL, Redis, etc.
|
||||
|
||||
In addition to managing HTTP based applications, Pomerium can be used to protect non-HTTP systems with the same consistent authorization policy. This is achieved by tunneling TCP over HTTP with the help of a client side command built into [`pomerium-cli`](/docs/installation.md#pomerium-cli).
|
||||
In addition to managing HTTP based applications, Pomerium can be used to protect non-HTTP systems with the same consistent authorization policy. This is achieved by tunneling TCP over HTTP with the help of a client side command built into [`pomerium-cli`](/docs/releases.md#pomerium-cli).
|
||||
|
||||
|
||||
Internally, Pomerium uses the [`CONNECT` method](https://developer.mozilla.org/en-US/docs/Web/HTTP/Methods/CONNECT) to establish the TCP tunnel.
|
||||
|
|
@ -26,7 +26,7 @@ Otherwise, the HTTP proxy in front of Pomerium must know how to properly handle
|
|||
|
||||
## Configuring
|
||||
|
||||
TCP configuration is simple. Just specify the correct scheme and ports in your policy [`to`](/reference/#to) and [`from`](/reference/#from) fields.
|
||||
TCP configuration is simple. Just specify the correct scheme and ports in your policy [`to`](/reference/readme.md#to) and [`from`](/reference/readme.md#from) fields.
|
||||
|
||||
Example:
|
||||
```yaml
|
||||
|
|
@ -47,7 +47,7 @@ Notes:
|
|||
|
||||
## Using
|
||||
|
||||
While HTTP routes can be consumed with just a normal browser, `pomerium-cli` must serve as a proxy for TCP routes. It is [available](/docs/installation.md#pomerium-cli) for a variety of platforms in various formats.
|
||||
While HTTP routes can be consumed with just a normal browser, `pomerium-cli` must serve as a proxy for TCP routes. It is [available](/docs/releases.md#pomerium-cli) for a variety of platforms in various formats.
|
||||
|
||||
To connect, you normally need just the external hostname and port of your TCP route:
|
||||
|
||||
|
|
|
|||
|
|
@ -43,11 +43,11 @@ To update your policies for v0.14, please remove any identity provider prefix.
|
|||
|
||||
### Upstream load balancing
|
||||
|
||||
With the v0.13 release, routes may contain [multiple `to` URLs](/reference/#to), and Pomerium will load balance between the endpoints. This allows Pomerium to fill the role of an edge proxy without the need for additional HTTP load balancers.
|
||||
With the v0.13 release, routes may contain [multiple `to` URLs](/reference/readme.md#to), and Pomerium will load balance between the endpoints. This allows Pomerium to fill the role of an edge proxy without the need for additional HTTP load balancers.
|
||||
|
||||
- Active [health checks](/reference/#health-checks) and passive [outlier detection](/reference/#outlier-detection)
|
||||
- Configurable [load balancing policies](/reference/#load-balancing-policy)
|
||||
- Configurable [load balancing weight](/reference/#to)
|
||||
- Active [health checks](/reference/readme.md#health-checks) and passive [outlier detection](/reference/readme.md#outlier-detection)
|
||||
- Configurable [load balancing policies](/reference/readme.md#load-balancing-policy)
|
||||
- Configurable [load balancing weight](/reference/readme.md#to)
|
||||
|
||||
See [Load Balancing](/docs/topics/load-balancing) for more information on using this feature set.
|
||||
|
||||
|
|
@ -57,7 +57,7 @@ With the v0.13 release, all TLS files referenced from Pomerium's configuration a
|
|||
|
||||
### Proxy Protocol support
|
||||
|
||||
The Pomerium HTTP listener now [supports](/reference/#use-proxy-protocol) HAPROXY's [proxy protocol](https://www.haproxy.org/download/1.9/doc/proxy-protocol.txt) to update `X-Forwarded-For` accurately when behind another proxy service.
|
||||
The Pomerium HTTP listener now [supports](/reference/readme.md#use-proxy-protocol) HAPROXY's [proxy protocol](https://www.haproxy.org/download/1.9/doc/proxy-protocol.txt) to update `X-Forwarded-For` accurately when behind another proxy service.
|
||||
|
||||
## Breaking
|
||||
|
||||
|
|
@ -88,7 +88,7 @@ Pomerium can now be used for non-HTTP services. See [documentation](/docs/topic
|
|||
|
||||
### Datadog Tracing
|
||||
|
||||
Datadog has been added as a natively supported [tracing backend](/reference/#datadog)
|
||||
Datadog has been added as a natively supported [tracing backend](/reference/readme.md#datadog)
|
||||
|
||||
# Since 0.10.0
|
||||
|
||||
|
|
@ -310,7 +310,7 @@ Please see the updated examples, and [cache service docs] as a reference and for
|
|||
|
||||
- Okta no longer uses tokens to retrieve group membership. [Group membership](https://developer.okta.com/docs/reference/api/groups/) is now fetched using Okta's API.
|
||||
- Okta's group membership is now determined by the globally unique and immutable ID field. Please update your policies to use group `ID` instead of group name.
|
||||
- Okta now requires an additional set of credentials to be used to query for group membership set as a [service account](https://www.pomerium.io/docs/reference/reference.html#identity-provider-service-account).
|
||||
- Okta now requires an additional set of credentials to be used to query for group membership set as a [service account](/reference/readme.md#identity-provider-service-account).
|
||||
|
||||
### OneLogin
|
||||
|
||||
|
|
@ -322,7 +322,7 @@ Force refresh has been removed from the dashboard. Logging out and back in again
|
|||
|
||||
### Programmatic Access API changed
|
||||
|
||||
Previous programmatic authentication endpoints (`/api/v1/token`) has been removed and has been replaced by a per-route, oauth2 based auth flow. Please see updated [programmatic documentation](https://www.pomerium.io/docs/reference/programmatic-access.html) how to use the new programmatic access api.
|
||||
Previous programmatic authentication endpoints (`/api/v1/token`) has been removed and has been replaced by a per-route, oauth2 based auth flow. Please see updated [programmatic documentation](/docs/topics/programmatic-access.md) how to use the new programmatic access api.
|
||||
|
||||
### Forward-auth route change
|
||||
|
||||
|
|
@ -473,9 +473,9 @@ Usage of the POLICY_FILE envvar is no longer supported. Support for file based p
|
|||
|
||||
The configuration variable [Authenticate Internal Service URL] must now be a valid [URL](https://golang.org/pkg/net/url/#URL) type and contain both a hostname and valid `https` schema.
|
||||
|
||||
[authenticate internal service url]: ../reference/readme.md#authenticate-service-url
|
||||
[cache service docs]: ../reference/readme.md#cache-service
|
||||
[identity provider service account]: ../reference/readme.md#identity-provider-service-account
|
||||
[policy]: ../reference/readme.md#policy
|
||||
[storage backend configuration here]: ../reference/readme.md#cache-service
|
||||
[storage backend types]: ../reference/readme.md#data-broker-storage-type
|
||||
[authenticate internal service url]: /reference/readme.md#authenticate-service-url
|
||||
[cache service docs]: /reference/readme.md#data-broker-service
|
||||
[identity provider service account]: /reference/readme.md#identity-provider-service-account
|
||||
[policy]: /reference/readme.md#policy
|
||||
[storage backend configuration here]: /reference/readme.md#data-broker-service
|
||||
[storage backend types]: /reference/readme.md#data-broker-storage-type
|
||||
|
|
|
|||
|
|
@ -67,7 +67,7 @@ settings:
|
|||
A Policy defines what permissions a set of users or groups has. Policies are applied to Namespaces or Routes to associate the set of permissions with a service or set of service, completing the authentication model.
|
||||
|
||||
::: tip
|
||||
This is a separate concept from [policies](../reference/#policy) in the non-enterprise model. In open-source Pomerium, the `policy` block defines both routes and access.
|
||||
This is a separate concept from [policies](/reference/readme.md#policy) in the non-enterprise model. In open-source Pomerium, the `policy` block defines both routes and access.
|
||||
:::
|
||||
|
||||
Policies can be constructed three ways:
|
||||
|
|
|
|||
|
|
@ -35,7 +35,7 @@ One of the advantages of a Kubernetes deployment is automatic scaling, but if yo
|
|||
|
||||
## Issue a Certificate
|
||||
|
||||
This setup assumes an existing certificate solution using cert-manager, as described in [Pomerium using Helm]. If you already have a different certificate solution, create and implement a certificate for `pomerium-console.pomerium.svc.cluster.local`. Then you can move on to [the next stage](#configure-kubernetes-for-pomerium).
|
||||
This setup assumes an existing certificate solution using cert-manager, as described in [Pomerium using Helm]. If you already have a different certificate solution, create and implement a certificate for `pomerium-console.pomerium.svc.cluster.local`. Then you can move on to [the next stage](#update-pomerium).
|
||||
|
||||
|
||||
1. Create a certificate configuration file for Pomerium Enterprise Our example is named `pomerium-console-certificate.yaml`:
|
||||
|
|
@ -140,5 +140,5 @@ If, while updating the open-source Pomerium values, you change any block's `serv
|
|||
kubectl delete svc pomerium-proxy
|
||||
```
|
||||
|
||||
[Pomerium using Helm]: /docs/quick-start/helm.md
|
||||
[Pomerium using Helm]: /docs/install/helm.md
|
||||
[cert-manager]: https://cert-manager.io/docs/
|
||||
|
|
@ -12,7 +12,7 @@ This document assumes:
|
|||
|
||||
- A non-containerized environment, either your local computer or a virtual machine (**vm**). While Pomerium is designed to scale with your production environment, we'll leave containerization and infrastructure as code (**IaC**) out for now, to focus on learning how Pomerium Enterprise works.
|
||||
- `root` or `sudo` privileges on the host.
|
||||
- You already have the open-source Pomerium base installed. If not, follow [this doc](/docs/quick-start/binary.md) before you continue.
|
||||
- You already have the open-source Pomerium base installed. If not, follow [this doc](/docs/install/binary.md) before you continue.
|
||||
- While an existing route is not required, we suggest implementing one test route to validate your identity provider (**IdP**) configuration.
|
||||
- Pomerium Enterprise requires a relational database. PostgreSQL 9+ is supported.
|
||||
- Securing the database connection with TLS may not be required, especially for a local installation, but is strongly recommended for production deployments. Therefor, this guide will assume a TLS-secured database connection.
|
||||
|
|
|
|||
|
|
@ -8,5 +8,5 @@ meta:
|
|||
|
||||
There are several ways to install Pomerium Enterprise, to suite your organization's needs. [Let us know] if you don't see an installation method compatible with your infrastructure.
|
||||
|
||||
- [Quickstart](./quickstart.md)
|
||||
- [Kubernetes with Helm](./helm.md)
|
||||
- [Quickstart](/enterprise/install/quickstart.md)
|
||||
- [Kubernetes with Helm](/enterprise/install/helm.md)
|
||||
|
|
@ -27,7 +27,7 @@ This value is only visible in the Console UI.
|
|||
|
||||
`From` is the externally accessible URL for the proxied request.
|
||||
|
||||
Specifying `tcp+https` for the scheme enables [TCP proxying](../docs/topics/tcp-support.md) support for the route. You may map more than one port through the same hostname by specifying a different `:port` in the URL.
|
||||
Specifying `tcp+https` for the scheme enables [TCP proxying](/docs/topics/tcp-support.md) support for the route. You may map more than one port through the same hostname by specifying a different `:port` in the URL.
|
||||
|
||||
#### To
|
||||
|
||||
|
|
@ -40,7 +40,7 @@ Specifying `tcp+https` for the scheme enables [TCP proxying](../docs/topics/tcp-
|
|||
- https://b.example.com
|
||||
```
|
||||
|
||||
A load balancing weight may be associated with a particular upstream by appending `,[weight]` to the URL. The exact behavior depends on your [`lb_policy`](#load-balancing-policy) setting. See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.html#load-balancing-weight).
|
||||
A load balancing weight may be associated with a particular upstream by appending `,[weight]` to the URL. The exact behavior depends on your [`lb_policy`](/reference/readme.md#load-balancing-policy) setting. See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.md#load-balancing-weight).
|
||||
|
||||
Must be `tcp` if `from` is `tcp+https`.
|
||||
|
||||
|
|
@ -153,7 +153,7 @@ If set, enables proxying of websocket connections.
|
|||
|
||||
:::warning
|
||||
|
||||
**Use with caution:** websockets are long-lived connections, so [global timeouts](#global-timeouts) are not enforced (though the policy-specific `timeout` is enforced). Allowing websocket connections to the proxy could result in abuse via [DOS attacks](https://www.cloudflare.com/learning/ddos/ddos-attack-tools/slowloris/).
|
||||
**Use with caution:** websockets are long-lived connections, so [global timeouts](/reference/readme.md#global-timeouts) are not enforced (though the policy-specific `timeout` is enforced). Allowing websocket connections to the proxy could result in abuse via [DOS attacks](https://www.cloudflare.com/learning/ddos/ddos-attack-tools/slowloris/).
|
||||
|
||||
:::
|
||||
|
||||
|
|
@ -255,14 +255,14 @@ See [Envoy documentation](https://www.envoyproxy.io/docs/envoy/latest/api-v3/con
|
|||
- [`RANDOM`](https://www.envoyproxy.io/docs/envoy/latest/intro/arch_overview/upstream/load_balancing/load_balancers#random)
|
||||
- [`MAGLEV`](https://www.envoyproxy.io/docs/envoy/latest/intro/arch_overview/upstream/load_balancing/load_balancers#maglev) and may be further configured using [`maglev_lb_config`](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/cluster/v3/cluster.proto#envoy-v3-api-msg-config-cluster-v3-cluster-maglevlbconfig) option
|
||||
|
||||
Some policy types support additional [configuration](#load-balancing-policy-config).
|
||||
Some policy types support additional [configuration](/reference/readme.md#load-balancing-policy-config).
|
||||
|
||||
## Policies
|
||||
|
||||
A Policy defines what permissions a set of users or groups has. Policies are applied to Namespaces or Routes to associate the set of permissions with a service or set of service, completing the authentication model.
|
||||
|
||||
::: tip
|
||||
This is a separate concept from [policies](../reference/#policy) in the non-enterprise model. In open-source Pomerium, the `policy` block defines both routes and access.
|
||||
This is a separate concept from [policies](/reference/readme.md#policy) in the non-enterprise model. In open-source Pomerium, the `policy` block defines both routes and access.
|
||||
:::
|
||||
|
||||
Policies can be constructed three ways:
|
||||
|
|
@ -319,7 +319,7 @@ The available criteria types are:
|
|||
- `time_of_day`
|
||||
- `user`
|
||||
|
||||
Some criteria also support a subpath as part of the criterion name:
|
||||
Some criteria also support a sub-path as part of the criterion name:
|
||||
|
||||
```yaml
|
||||
- allow:
|
||||
|
|
|
|||
|
|
@ -21,7 +21,7 @@ This guide covers using Pomerium to secure an instance of [code-server]. Pomeriu
|
|||
|
||||
[Visual Studio Code] is an open source code editor by Microsoft that has become [incredibly popular](https://insights.stackoverflow.com/survey/2019#technology-_-most-popular-development-environments) in the last few years. For many developers, [Visual Studio Code] hits the sweet spot between no frills editors like vim/emacs and full feature IDE's like Eclipse and IntelliJ. VS Code offers some of the creature comforts like intellisense, git integration, and plugins, while staying relatively lightweight.
|
||||
|
||||
One of the interesting attributes of [Visual Studio Code] is that it is built on the [Electron](<https://en.wikipedia.org/wiki/Electron_(software_framework)>) framework which uses a headless instance of Chrome rendered as a desktop application. It didn't take long for folks to realize that if we already had this great IDE written in Javascript, it may be possible to make [Visual Studio Code] run remotely.
|
||||
One of the interesting attributes of [Visual Studio Code] is that it is built on the [Electron](https://en.wikipedia.org/wiki/Electron_(software_framework)) framework which uses a headless instance of Chrome rendered as a desktop application. It didn't take long for folks to realize that if we already had this great IDE written in Javascript, it may be possible to make [Visual Studio Code] run remotely.
|
||||
|
||||
> "Any application that can be written in JavaScript, will eventually be written in JavaScript." -- [Jeff Atwood](https://blog.codinghorror.com/the-principle-of-least-power/)
|
||||
|
||||
|
|
@ -33,7 +33,7 @@ One of the interesting attributes of [Visual Studio Code] is that it is built on
|
|||
|
||||
## Pre-requisites
|
||||
|
||||
This guide assumes you have already completed one of the [quick start] guides, and have a working instance of Pomerium up and running. For purpose of this guide, I'm going to use docker-compose, though any other deployment method would work equally well.
|
||||
This guide assumes you have already completed one of the [install] guides, and have a working instance of Pomerium up and running. For purpose of this guide, I'm going to use docker-compose, though any other deployment method would work equally well.
|
||||
|
||||
## Configure
|
||||
|
||||
|
|
@ -129,7 +129,7 @@ When the code-server container is rebuilt, any files outside of `/home/coder/pro
|
|||
|
||||
[integrated terminal]: https://code.visualstudio.com/docs/editor/integrated-terminal
|
||||
[path]: https://en.wikipedia.org/wiki/PATH_(variable)
|
||||
[quick start]: ../docs/quick-start
|
||||
[synology nas]: ./synology.md
|
||||
[install]: /docs/install/readme.md
|
||||
[synology nas]: /guides/synology.md
|
||||
[visual studio code]: https://code.visualstudio.com/
|
||||
[code-server]: https://github.com/cdr/code-server
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ description: >-
|
|||
|
||||
# Local OIDC Provider
|
||||
|
||||
You can use the same below configs for other supported [identity providers](/docs/identity-providers).
|
||||
You can use the same below configs for other supported [identity providers](/docs/identity-providers/readme.md).
|
||||
|
||||
## Configure
|
||||
### Docker-compose
|
||||
|
|
@ -53,7 +53,7 @@ services:
|
|||
- 9000:9000
|
||||
```
|
||||
|
||||
You can generate certificates for `*.localhost.pomerium.io` using [this instruction](https://www.pomerium.io/docs/reference/certificates.html#certificates-2)
|
||||
You can generate certificates for `*.localhost.pomerium.io` using [this instruction](/docs/topics/certificates.md#certificates-2)
|
||||
|
||||
### Pomerium config
|
||||
|
||||
|
|
@ -151,5 +151,5 @@ $ docker-compose up -d
|
|||
|
||||
Now accessing to `https://verify.localhost.pomerium.io` and you will be redireted to OIDC server for authentication.
|
||||
|
||||
[identity provider]: ../docs/identity-providers/
|
||||
[identity provider]: ../docs/identity-providers/readme.md
|
||||
[qlik/simple-oidc-provider]: https://hub.docker.com/r/qlik/simple-oidc-provider/
|
||||
|
|
|
|||
|
|
@ -215,12 +215,12 @@ And just to be safe, try logging in from another google account to see what happ
|
|||
|
||||

|
||||
|
||||
[certificate documentation]: ../topics/certificates.md
|
||||
[configuration variable docs]: ../../reference/readme.md
|
||||
[certificate documentation]: /docs/topics/certificates.md
|
||||
[configuration variable docs]: /reference/readme.md
|
||||
[diskstation manager]: https://www.synology.com/en-us/dsm
|
||||
[docker-capable]: https://www.synology.com/en-us/dsm/packages/Docker
|
||||
[httpbin]: https://httpbin.org
|
||||
[identity provider]: ../identity-providers/readme.md
|
||||
[identity provider]: /docs/identity-providers/readme.md
|
||||
[letsencrypt]: https://letsencrypt.org/
|
||||
[nginx]: https://www.nginx.com
|
||||
[self-hosted apps]: https://github.com/Kickball/awesome-selfhosted
|
||||
|
|
|
|||
|
|
@ -10,7 +10,7 @@ description: >-
|
|||
|
||||
# Securing TCP based services
|
||||
|
||||
The following guide demonstrates how to use Pomerium's [TCP Proxying](/topics/tcp-support.md) support with various TCP services such as databases and other non-HTTP protocols. It also covers integration points with them when possible.
|
||||
The following guide demonstrates how to use Pomerium's [TCP Proxying](/docs/topics/tcp-support.md) support with various TCP services such as databases and other non-HTTP protocols. It also covers integration points with them when possible.
|
||||
|
||||
The source files from this guide can be found on [GitHub](https://github.com/pomerium/pomerium/tree/master/examples/tcp/).
|
||||
|
||||
|
|
@ -25,7 +25,7 @@ Important notes:
|
|||
|
||||
## How it works
|
||||
|
||||
* Create a standard Pomerium configuration for your [identity provider (IdP)](/docs/identity-providers/)
|
||||
* Create a standard Pomerium configuration for your [identity provider (IdP)](/docs/identity-providers/readme.md)
|
||||
* `pomerium-cli` runs on your workstation, listening on loopback for TCP connections
|
||||
* When an inbound connection is made, `pomerium-cli` proxies the connection through `pomerium`, authenticating the user if needed
|
||||
* Pomerium authorizes the connection and forwards it to the upstream service
|
||||
|
|
@ -39,7 +39,7 @@ This recipe is designed to run on a local docker-compose instance. The included
|
|||
* docker-compose
|
||||
* A copy of the [example repo](https://github.com/pomerium/pomerium/tree/master/examples/tcp/) checked out
|
||||
* Valid credentials for your OIDC provider
|
||||
* The [Pomerium Client](/docs/installation.md#pomerium-cli) installed
|
||||
* The [Pomerium Client](/docs/releases.md#pomerium-cli) installed
|
||||
* (Optional) `mkcert` to generate locally trusted certificates
|
||||
|
||||
## Certificates (optional)
|
||||
|
|
@ -82,7 +82,7 @@ Included in our compose file:
|
|||
|
||||
## Connect
|
||||
|
||||
To connect to your service, ensure [`pomerium-cli`](/docs/installation.md#pomerium-cli) is in your `$PATH` and run the `tcp` command, specifying the service you wish to reach.
|
||||
To connect to your service, ensure [`pomerium-cli`](/docs/releases.md#pomerium-cli) is in your `$PATH` and run the `tcp` command, specifying the service you wish to reach.
|
||||
|
||||
```bash
|
||||
pomerium-cli tcp [hostname]:[port]
|
||||
|
|
|
|||
|
|
@ -56,4 +56,4 @@ Navigate to your TiddlyWiki instance (e.g. `https://wiki.example.local`) and log
|
|||
|
||||
* as another email: pomerium displays a permission denied error.
|
||||
|
||||
[quick start]: ../docs/quick-start
|
||||
[quick start]: /docs/install/readme.md
|
||||
|
|
|
|||
|
|
@ -24,7 +24,7 @@ While there are software clients available to interact with the daemon over RPC,
|
|||
::: warning
|
||||
Because RPC traffic to and from a Transmission daemon is unencrypted, we strongly suggest you only communicate from Pomerium to Transmission on a trusted private network. Note that some cloud hosting providers differentiate "private networking" (which is visible to all hosts in a data center) from "VLANS" which are only visible to your hosts. While you can configure a local proxy on your Transmission host to provide TLS encryption, that configuration is outside of the scope of this guide.
|
||||
|
||||
Running Pomerium and Transmission on the same host, using [docker](../docs/quick-start) for example, negates this concern.
|
||||
Running Pomerium and Transmission on the same host, using [docker](/docs/install/readme.md) for example, negates this concern.
|
||||
:::
|
||||
|
||||
## Before You Begin
|
||||
|
|
@ -109,4 +109,4 @@ You should now be able to authenticate and access your Transmission daemon remot
|
|||
In addition to the lock symbol in your browser's address bar, you can go to `<transmission.mydomain.com>/.pomerium` to view and confirm your session details.
|
||||
|
||||
[Transmission]: https://transmissionbt.com/
|
||||
[quick start]: ../docs/quick-start
|
||||
[quick start]: /docs/install/readme.md
|
||||
|
|
@ -46,7 +46,7 @@ Address specifies the host and port to serve HTTP requests from. If empty, `:443
|
|||
- Type: `bool`
|
||||
- Optional
|
||||
|
||||
Turning on autocert allows Pomerium to automatically retrieve, manage, and renew public facing TLS certificates from [Let's Encrypt][letsencrypt] which includes managed routes and the authenticate service. [Autocert Directory](./#autocert-directory) must be used with Autocert must have a place to persist, and share certificate data between services. Note that autocert also provides [OCSP stapling](https://en.wikipedia.org/wiki/OCSP_stapling).
|
||||
Turning on autocert allows Pomerium to automatically retrieve, manage, and renew public facing TLS certificates from [Let's Encrypt][letsencrypt] which includes managed routes and the authenticate service. [Autocert Directory](#autocert-directory) must be used with Autocert must have a place to persist, and share certificate data between services. Note that autocert also provides [OCSP stapling](https://en.wikipedia.org/wiki/OCSP_stapling).
|
||||
|
||||
This setting can be useful in situations where you may not have Pomerium behind a TLS terminating ingress or proxy that is already handling your public certificates on your behalf.
|
||||
|
||||
|
|
@ -69,7 +69,7 @@ Autocert requires that ports `80`/`443` be accessible from the internet in order
|
|||
- Type: `bool`
|
||||
- Optional
|
||||
|
||||
If true, force autocert to request a certificate with the `status_request` extension (commonly called `Must-Staple`). This allows the TLS client (_id est_ the browser) to fail immediately if the TLS handshake doesn't include OCSP stapling information. This setting is only used when [Autocert](./#autocert) is true.
|
||||
If true, force autocert to request a certificate with the `status_request` extension (commonly called `Must-Staple`). This allows the TLS client (_id est_ the browser) to fail immediately if the TLS handshake doesn't include OCSP stapling information. This setting is only used when [Autocert](#autocert) is true.
|
||||
|
||||
:::tip
|
||||
|
||||
|
|
@ -84,7 +84,7 @@ For more details, please see [RFC7633](https://tools.ietf.org/html/rfc7633) .
|
|||
- Environmental Variable: either `AUTOCERT_DIR`
|
||||
- Config File Key: `autocert_dir`
|
||||
- Type: `string` pointing to the path of the directory
|
||||
- Required if using [Autocert](./#autocert) setting
|
||||
- Required if using [Autocert](#autocert) setting
|
||||
- Default:
|
||||
|
||||
- `/data/autocert` in published Pomerium docker images
|
||||
|
|
@ -339,7 +339,7 @@ services:
|
|||
- Example: `TIMEOUT_READ=30s`
|
||||
- Defaults: `TIMEOUT_READ=30s` `TIMEOUT_WRITE=0` `TIMEOUT_IDLE=5m`
|
||||
|
||||
Timeouts set the global server timeouts. Timeouts can also be set for individual [routes](./#policy).
|
||||
Timeouts set the global server timeouts. Timeouts can also be set for individual [routes](#policy).
|
||||
|
||||
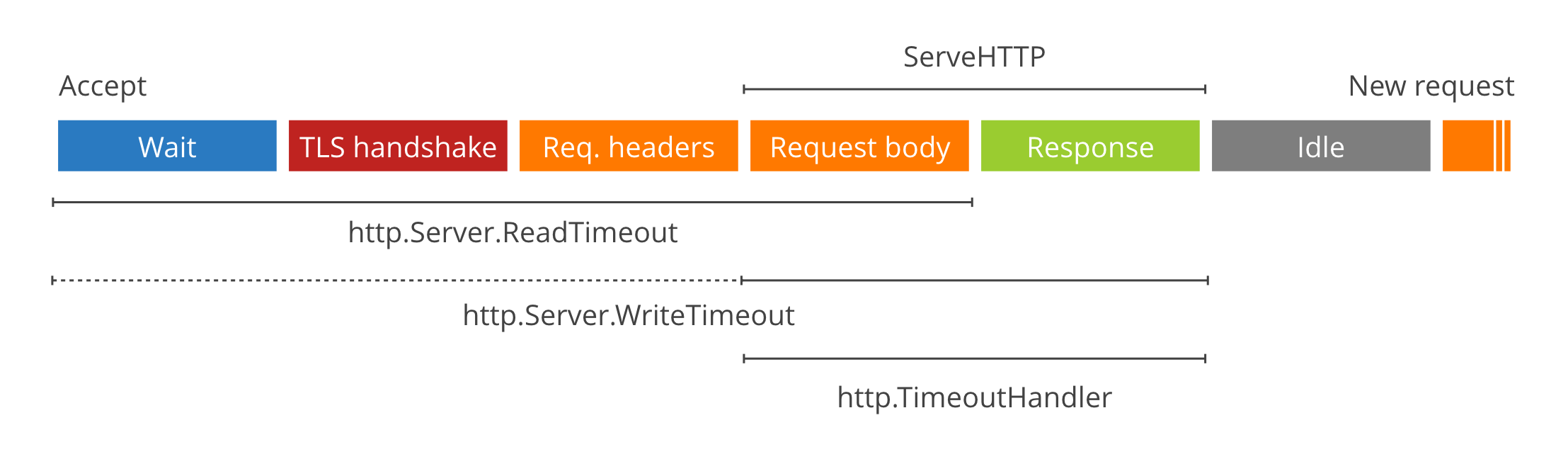
|
||||
|
||||
|
|
@ -1174,7 +1174,7 @@ Allow unauthenticated HTTP OPTIONS requests as [per the CORS spec](https://devel
|
|||
|
||||
Enable sending a signed [Authorization Header](https://cloud.google.com/run/docs/authenticating/service-to-service) to upstream GCP services.
|
||||
|
||||
Requires setting [Google Cloud Serverless Authentication Service Account](./#google-cloud-serverless-authentication-service-account) or running Pomerium in an environment with a GCP service account present in default locations.
|
||||
Requires setting [Google Cloud Serverless Authentication Service Account](#google-cloud-serverless-authentication-service-account) or running Pomerium in an environment with a GCP service account present in default locations.
|
||||
|
||||
|
||||
### From
|
||||
|
|
@ -1454,7 +1454,7 @@ Either `redirect` or `to` must be set.
|
|||
- https://b.example.com
|
||||
```
|
||||
|
||||
A load balancing weight may be associated with a particular upstream by appending `,[weight]` to the URL. The exact behavior depends on your [`lb_policy`](#load-balancing-policy) setting. See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.html#load-balancing-weight).
|
||||
A load balancing weight may be associated with a particular upstream by appending `,[weight]` to the URL. The exact behavior depends on your [`lb_policy`](#load-balancing-policy) setting. See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.md#load-balancing-weight).
|
||||
|
||||
Must be `tcp` if `from` is `tcp+https`.
|
||||
|
||||
|
|
@ -1585,7 +1585,7 @@ When [`lb_policy`](#load-balancing-policy) is configured, you may further custom
|
|||
- [`ring_hash_lb_config`](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/cluster/v3/cluster.proto#config-cluster-v3-cluster-ringhashlbconfig)
|
||||
- [`maglev_lb_config`](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/cluster/v3/cluster.proto#envoy-v3-api-msg-config-cluster-v3-cluster-maglevlbconfig)
|
||||
|
||||
See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.html#load-balancing-method)
|
||||
See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.md#load-balancing-method)
|
||||
|
||||
|
||||
### Health Checks
|
||||
|
|
@ -1605,7 +1605,7 @@ Only one of `http_health_check`, `tcp_health_check`, or `grpc_health_check` may
|
|||
- [HTTP](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/health_check.proto#envoy-v3-api-msg-config-core-v3-healthcheck-httphealthcheck)
|
||||
- [GRPC](https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/health_check.proto#envoy-v3-api-msg-config-core-v3-healthcheck-grpchealthcheck)
|
||||
|
||||
See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.html#active-health-checks).
|
||||
See [Load Balancing](/docs/topics/load-balancing) for example [configurations](/docs/topics/load-balancing.md#active-health-checks).
|
||||
|
||||
|
||||
### Websocket Connections
|
||||
|
|
@ -1707,12 +1707,12 @@ Be aware that any RSA based signature method may be an order of magnitude lower
|
|||
[base64 encoded]: https://en.wikipedia.org/wiki/Base64
|
||||
[elliptic curve]: https://wiki.openssl.org/index.php/Command_Line_Elliptic_Curve_Operations#Generating_EC_Keys_and_Parameters
|
||||
[environmental variables]: https://en.wikipedia.org/wiki/Environment_variable
|
||||
[identity provider]: ../docs/identity-providers/
|
||||
[identity provider]: /docs/identity-providers/readme.md
|
||||
[json]: https://en.wikipedia.org/wiki/JSON
|
||||
[letsencrypt]: https://letsencrypt.org/
|
||||
[oidc rfc]: https://openid.net/specs/openid-connect-core-1_0.html#AuthRequest
|
||||
[okta]: ../docs/identity-providers/okta.md
|
||||
[okta]: /docs/identity-providers/okta.md
|
||||
[script]: https://github.com/pomerium/pomerium/blob/master/scripts/generate_wildcard_cert.sh
|
||||
[signed headers]: ../docs/topics/getting-users-identity.md
|
||||
[signed headers]: /docs/topics/getting-users-identity.md
|
||||
[toml]: https://en.wikipedia.org/wiki/TOML
|
||||
[yaml]: https://en.wikipedia.org/wiki/YAML
|
||||
|
|
|
|||
|
|
@ -65,7 +65,7 @@ settings:
|
|||
- Type: `bool`
|
||||
- Optional
|
||||
doc: |
|
||||
Turning on autocert allows Pomerium to automatically retrieve, manage, and renew public facing TLS certificates from [Let's Encrypt][letsencrypt] which includes managed routes and the authenticate service. [Autocert Directory](./#autocert-directory) must be used with Autocert must have a place to persist, and share certificate data between services. Note that autocert also provides [OCSP stapling](https://en.wikipedia.org/wiki/OCSP_stapling).
|
||||
Turning on autocert allows Pomerium to automatically retrieve, manage, and renew public facing TLS certificates from [Let's Encrypt][letsencrypt] which includes managed routes and the authenticate service. [Autocert Directory](#autocert-directory) must be used with Autocert must have a place to persist, and share certificate data between services. Note that autocert also provides [OCSP stapling](https://en.wikipedia.org/wiki/OCSP_stapling).
|
||||
|
||||
This setting can be useful in situations where you may not have Pomerium behind a TLS terminating ingress or proxy that is already handling your public certificates on your behalf.
|
||||
|
||||
|
|
@ -90,7 +90,7 @@ settings:
|
|||
- Type: `bool`
|
||||
- Optional
|
||||
doc: |
|
||||
If true, force autocert to request a certificate with the `status_request` extension (commonly called `Must-Staple`). This allows the TLS client (_id est_ the browser) to fail immediately if the TLS handshake doesn't include OCSP stapling information. This setting is only used when [Autocert](./#autocert) is true.
|
||||
If true, force autocert to request a certificate with the `status_request` extension (commonly called `Must-Staple`). This allows the TLS client (_id est_ the browser) to fail immediately if the TLS handshake doesn't include OCSP stapling information. This setting is only used when [Autocert](#autocert) is true.
|
||||
|
||||
:::tip
|
||||
|
||||
|
|
@ -105,7 +105,7 @@ settings:
|
|||
- Environmental Variable: either `AUTOCERT_DIR`
|
||||
- Config File Key: `autocert_dir`
|
||||
- Type: `string` pointing to the path of the directory
|
||||
- Required if using [Autocert](./#autocert) setting
|
||||
- Required if using [Autocert](#autocert) setting
|
||||
- Default:
|
||||
|
||||
- `/data/autocert` in published Pomerium docker images
|
||||
|
|
@ -387,7 +387,7 @@ settings:
|
|||
- Example: `TIMEOUT_READ=30s`
|
||||
- Defaults: `TIMEOUT_READ=30s` `TIMEOUT_WRITE=0` `TIMEOUT_IDLE=5m`
|
||||
doc: |
|
||||
Timeouts set the global server timeouts. Timeouts can also be set for individual [routes](./#policy).
|
||||
Timeouts set the global server timeouts. Timeouts can also be set for individual [routes](#policy).
|
||||
|
||||

|
||||
|
||||
|
|
@ -1300,7 +1300,7 @@ settings:
|
|||
doc: |
|
||||
Enable sending a signed [Authorization Header](https://cloud.google.com/run/docs/authenticating/service-to-service) to upstream GCP services.
|
||||
|
||||
Requires setting [Google Cloud Serverless Authentication Service Account](./#google-cloud-serverless-authentication-service-account) or running Pomerium in an environment with a GCP service account present in default locations.
|
||||
Requires setting [Google Cloud Serverless Authentication Service Account](#google-cloud-serverless-authentication-service-account) or running Pomerium in an environment with a GCP service account present in default locations.
|
||||
- name: "From"
|
||||
keys: ["from"]
|
||||
attributes: |
|
||||
|
|
@ -1312,7 +1312,7 @@ settings:
|
|||
doc: |
|
||||
`From` is the externally accessible URL for the proxied request.
|
||||
|
||||
Specifying `tcp+https` for the scheme enables [TCP proxying](../docs/topics/tcp-support.md) support for the route. You may map more than one port through the same hostname by specifying a different `:port` in the URL.
|
||||
Specifying `tcp+https` for the scheme enables [TCP proxying](/docs/topics/tcp-support.md) support for the route. You may map more than one port through the same hostname by specifying a different `:port` in the URL.
|
||||
- name: "Kubernetes Service Account Token"
|
||||
keys:
|
||||
[
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue