mirror of
https://github.com/pomerium/pomerium.git
synced 2025-08-01 16:01:26 +02:00
docs: update branding (#2435)
- add svg logos - adjust colors - add favicon - remove outdated demo Signed-off-by: Bobby DeSimone <bobbydesimone@gmail.com>
This commit is contained in:
parent
490a5f863a
commit
5d04531024
12 changed files with 65 additions and 35 deletions
Binary file not shown.
|
|
@ -23,23 +23,6 @@ Pomerium can be used to:
|
|||
- perform delegated user authorization for service-based authorization systems:
|
||||
- [Istio](/guides/istio.md)
|
||||
- [Google Cloud](/guides/cloud-run.md)
|
||||
- provide unified identity attestation for upstream services:
|
||||
- [Kubernetes](/guides/kubernetes.md)
|
||||
- [Grafana](/guides/istio.md#pomerium-configuration)
|
||||
- [Custom applications](/docs/topics/getting-users-identity.md)
|
||||
- provide a **VPN alternative**.
|
||||
- add unified access and identity to [custom, on-prem, and hosted apps and services](https://www.pomerium.com/integrations/)
|
||||
- serve as a **VPN alternative**.
|
||||
|
||||
## Demo
|
||||
|
||||
To make this a bit more concrete, click the image thumbnail to see a short youtube demo:
|
||||
|
||||
[](https://www.youtube.com/watch?v=ddmrkvBSO60 "Pomerium demo")
|
||||
|
||||
The above video shows the flow for both an unauthorized and authorized user.
|
||||
|
||||
1. An **unauthorized** user authenticates with their corporate single-sign-on provider.
|
||||
2. The **unauthorized** user is blocked from a protected resource.
|
||||
3. The **unauthorized** user signs out from their session.
|
||||
4. An **authorized** user authenticates with their corporate single-sign-on provider.
|
||||
5. Pomerium delegates and grants access to the requested resource.
|
||||
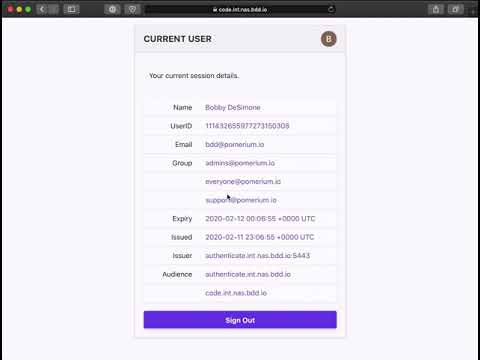
6. The **authorized** user inspects their user details including group membership.
|
||||
|
|
|
|||
|
|
@ -101,7 +101,7 @@ See the [README](https://github.com/pomerium/pomerium-helm/blob/master/charts/po
|
|||
|
||||
::: tip
|
||||
|
||||
Officially supported build platforms are limited by [envoy proxy](https://www.envoyproxy.io/). If you have an enoy binary for your platform in your path at start time, `pomerium` should function correctly.
|
||||
Officially supported build platforms are limited by [envoy proxy](https://www.envoyproxy.io/).
|
||||
|
||||
:::
|
||||
|
||||
|
|
|
|||
Binary file not shown.
|
|
@ -24,7 +24,7 @@ Ed25519 is no longer supported for `signing_key` since OPA Rego only supports EC
|
|||
Routes and policies may now be configured under a new top level key - `routes`
|
||||
|
||||
- This more closely aligns to how policies and routes are conceptually related
|
||||
- The `routes` block supports a more powerful syntax for definiting policies with conditionals and various criteria
|
||||
- The `routes` block supports a more powerful syntax for defining policies with conditionals and various criteria
|
||||
|
||||
### Support environmental proxy settings
|
||||
|
||||
|
|
@ -176,7 +176,7 @@ Please see the following interfaces for reference to implement your storage back
|
|||
|
||||
### Identity headers
|
||||
|
||||
With this release, pomerium will not insert identity headers (X-Pomerium-Jwt-Asserttion/X-Pomerium-Claim-*) by default. To get pre 0.9.0 behavior, you can set `pass_identity_headers` to true on a per-policy basis.
|
||||
With this release, pomerium will not insert identity headers (X-Pomerium-Jwt-Assertion/X-Pomerium-Claim-*) by default. To get pre 0.9.0 behavior, you can set `pass_identity_headers` to true on a per-policy basis.
|
||||
|
||||
# Since 0.8.0
|
||||
|
||||
|
|
|
|||
Loading…
Add table
Add a link
Reference in a new issue